
What Are the 7 Stages of the System Development Life Cycle?
Explore the 7 stages of the System Development Life Cycle (SDLC) focusing on login form security, MFA integration, and AI-driven authentication tools.
Explore the world of login security and user experience with Login4Website. Our blog features insights, tips, and news on AI-driven authentication solutions, free tools, and best practices for safeguarding your online presence.

Explore the 7 stages of the System Development Life Cycle (SDLC) focusing on login form security, MFA integration, and AI-driven authentication tools.

Explore cutting-edge social login form designs that combine UX best practices with advanced cybersecurity, featuring AI insights and MFA integration.
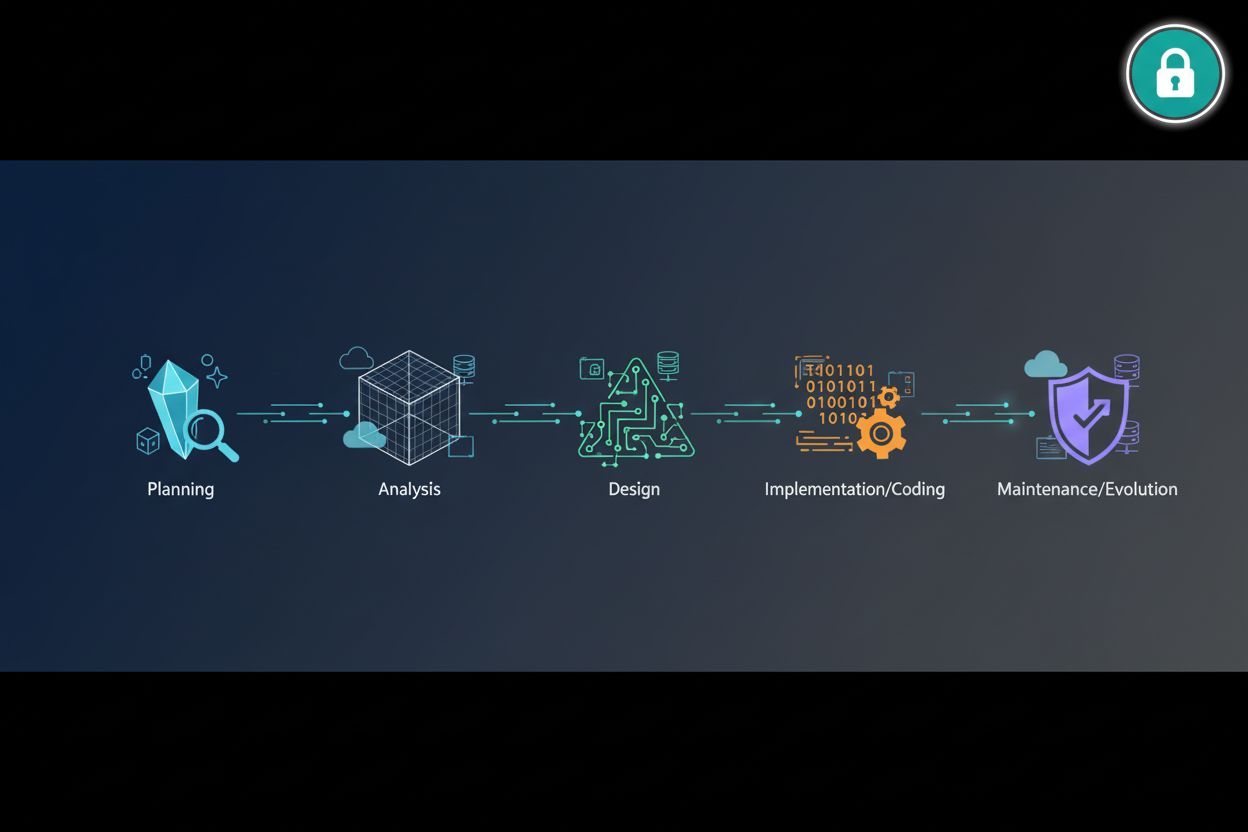
Explore the 5 phases of the System Development Life Cycle (SDLC) with a focus on login security, MFA integration, and AI-driven authentication best practices.

Discover the best practices for identity authentication. Enhance login security with MFA, SSO, AI, and UX design. Protect user data and prevent cyberattacks.

Learn how to develop a secure computer login system with best practices for cybersecurity, MFA, UX design, and AI integration. Protect your systems effectively.

Explore the 7 phases of the System Development Life Cycle (SDLC) and their application to designing secure and user-friendly login systems. Learn how to integrate cybersecurity best practices, MFA, and UX design principles.

Explore the Software Development Lifecycle (SDLC), its phases, models, and best practices. Learn how to build secure and high-quality software efficiently.

Learn how to use the Poison Queue Exchange pattern to enhance login form security, MFA integration, and overall system reliability. Implement robust error handling for improved authentication workflows.

Learn about shoulder surfing, a low-tech but effective cybersecurity threat. Discover prevention tips, the role of AI, MFA, and UX design in securing login forms. password management and authentication tools from visual eavesdropping.